Nowadays, with the cloud, you have a large number of companies offering backup solutions for your computers. The only problem for most of these solutions is that they are in the cloud, this results in:
- low recovery speed as you need to download again GB of data over a relatively slow connection;
- dependency on a third party and companies are going bust;
- possibly absence of a cloud offer matching your country regulations (location of the data) at a reasonable price.
If the cloud is not matching your requirements, here is a very simple solution based on external USB hard drive. The goal is not to be perfect but to be simple.
What you need is:
- an external hard drive, for example the WD Elements 2TB drive;
- a hardware token to store a long password, for example a Yubikey;
- a labeling machine, like a Brother P-touch;
- a safe at your bank;
- the ability to compute a bit in your head.
Everything is done on a Debian based system using the Gnome desktop. Read the full article before starting to follow the instructions.
First you need to store a long static password on your Yubikey. You should print a copy of the password and put in the safe at your bank for backup purpose.
Then, simply plug your USB drive into your computer and open the disk utility. Using the disk utility, stop the drive and remove the existing partition.
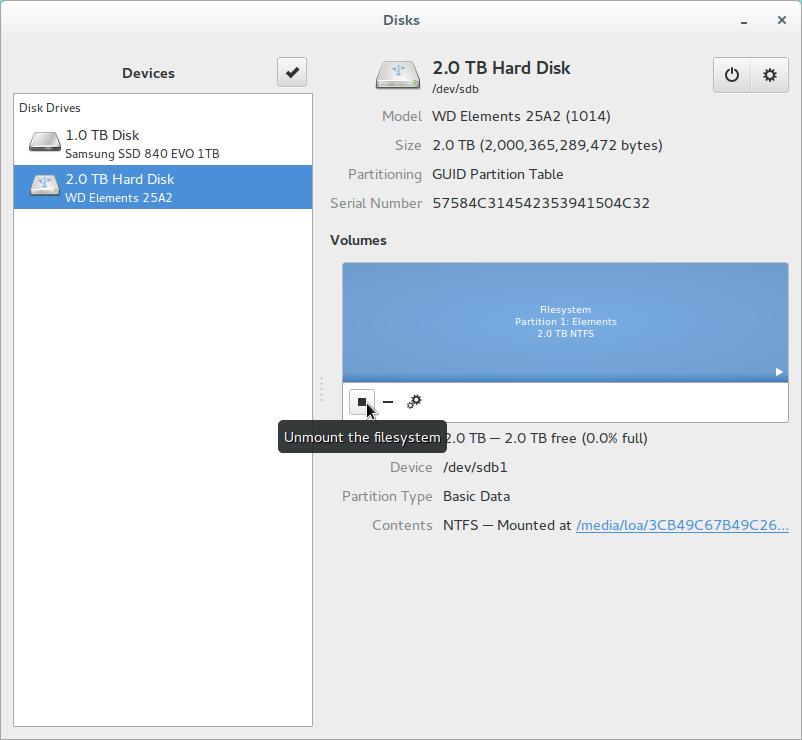
Then create a new encrypted partition.
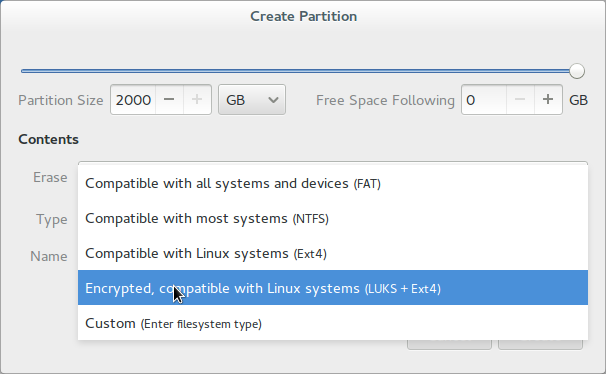
The passphrase is important: in my case, I have a simple to remember but hard to guess algorithm to generate the first part of the passphrase from the serial number of the hard drive. Think something in the line of using every second character but not the numbers and adding something in between. The second part is simply the long password from the Yubikey. Write down the algorithm on the paper with your backup of the long password and be sure to put the paper in the safe at your bank.
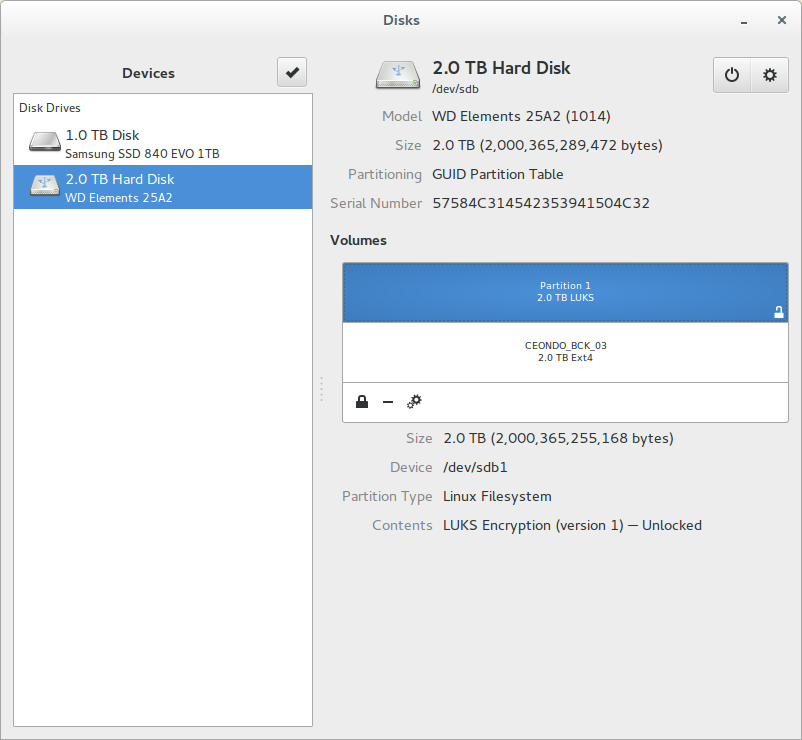
Now, you have an encrypted external hard drive. Because of the combination of an algorithm to compute the first part of the passphrase and the Yubikey (or any hardware token able to generate a password), it is easy for you to unlock the drive.
Now, every 2 to 4 weeks, just run a backup script to copy the full content of your laptop on the hard drive. The best is to use 2 hard drives and rotate them, keeping one in the safe at your bank. Once a drive is full, just buy a new one, never recycle the drives.
Do not forget to label your drives with your labeling machine. This is a picture of my first drive, it was full after 5 backups, as I just do a backup once a month, the costs stay at less than €200/year, which is fine.

In my case, this is combined with an automatic encrypted backup on a
remote server performed using rsync. The automatic backup does not
keep historical data like the backup on the USB drives but is
automatic.
The backup script in use is this one. Note that I have special case to
backup VMWare virtual machines which are not stored in the user home
directory. This is for performance reason, the /home/vmware
directory is not encrypted but the home directory is.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 | |
At the end, a simple and worry free strategy.

